- A new phishing campaign attempts to steal Office 365 login credentials by trying to convince users to accept a new Terms of Use and Privacy Policy.
- The attacker is using Google Ad Services to redirect users so this person or organization probably paid to have the URL go through an authorized source.
- One way to stay out of trouble is to keep yourself informed. Read more about this in our Security section.
- Have you read the latest news from the digital universe? Go through our News Hub to stay up to date.

It wasn’t a boring moment for attackers and scammers in luring Office 365 users.
Some phishing campaigns are using renewal warning messages, others are even trying to use the Office 365 voicemails to steal your data.
They even use calendar invites to break the increasingly work-from-home users accounts.
The newest threat is coming from a phishing campaign that attempts to steal Office 365 login credentials by trying to convince users to accept a new Terms of Use and Privacy Policy.
The phishing campaign targets secure email gateways (SEGs)
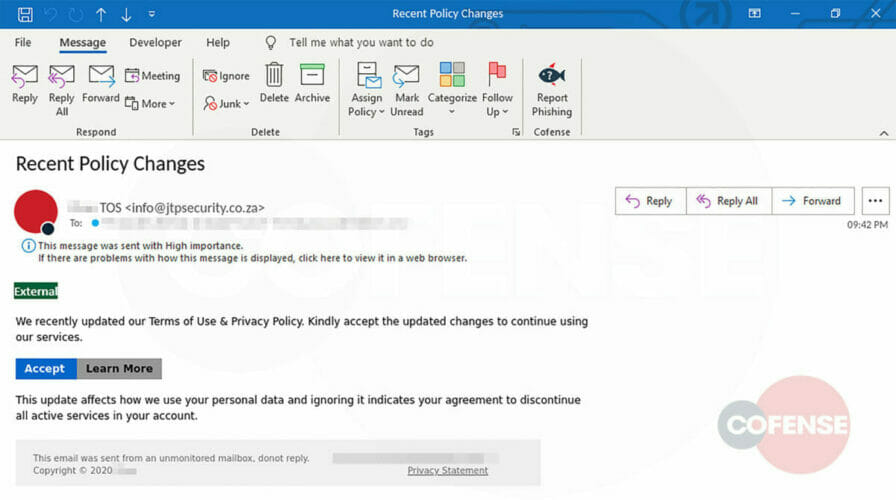
Cofense Phishing Defense Center (PDC) researchers who spotted this campaign describes the modus operandi of the phishing threat:
At first glance, the user will see This message was sent with High Importance. Again, the from address contains the word security and the subject talks about a Recent Policy Change, creating urgency to click and handle the matter immediately.
The email body talks about accepting the newly updated Terms of Use & Privacy Policy. Also, it notes how this new policy will affect personal data and discontinue all active services on the user’s account. Curious users will likely want to Learn More.
The attacker is using Google Ad Services to redirect users so this person or organization probably paid to have the URL go through an authorized source.
According to Cofense, this bypasses secure email gateways and exposes users to the phish.
If you click on either of the buttons presented, you are redirected to a duplicate of the real Microsoft page.
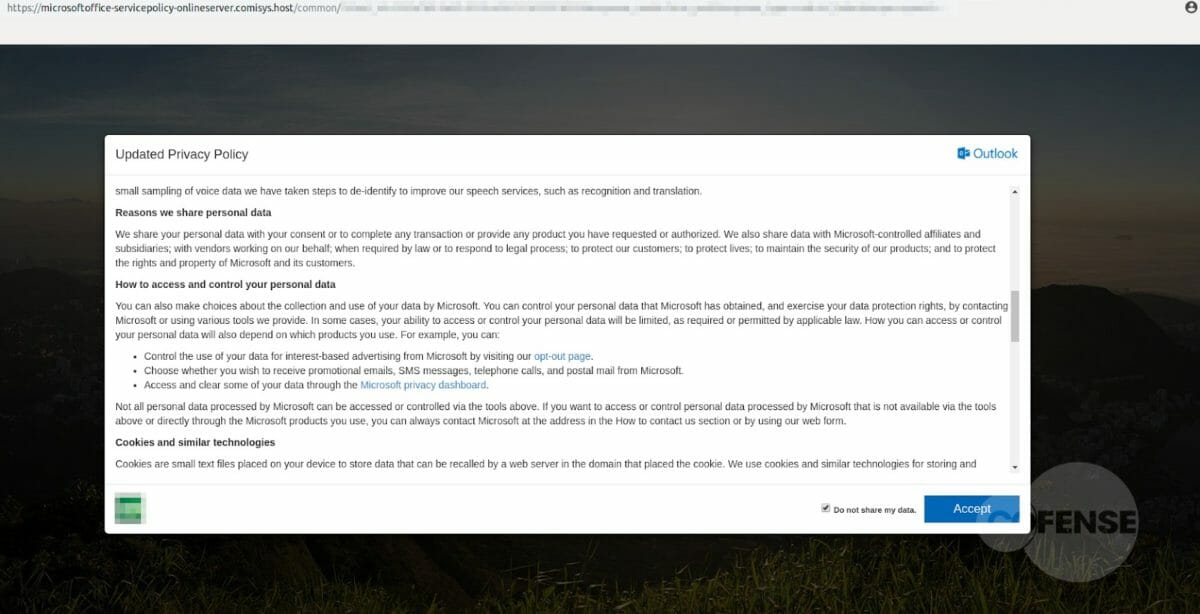
On that page, you will see a pop up of the privacy policy (taken from Microsoft’s website) and some logos that seem to be legitimate.
The next step is to be redirected again to a fake Microsoft login page. Needless to say that if you complete the credentials you will provide them to the phishing attacker.
Nothing sets a red flag since the next message on the screen ensures you that you have updated the terms and this time you are redirected to the legitimate Microsoft page, their Service Agreement.
How to stay safe? Make absolutely sure when clicking on unsolicited e-mails and links.
Have you been a victim of this phishing scam? Tell us all about it in the Comments section below.
Thank you for viewing the article, if you find it interesting, you can support us by buying at the link:: https://officerambo.com/shop/
No comments:
Post a Comment